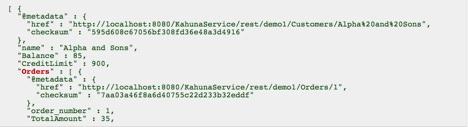
[caption id="attachment_16395" align="aligncenter" width="551"] "Smart" tvs are among the 100K non-PCs turned my malware into Thingbots.[/caption] More than a quarter of the 750,000 malicious emails sent by a sophisticated botnet during the last days of 2013 were sent not by malware-addled zombie computers, but by "Thingbots": Malware-addled zombie computers built into consumer electronics and other "smart" gadgets or appliances. A new report found that more than 750,000 phishing and spam messages sent between Dec. 23 and Jan. 6 turned out to originate from a botnet whose thralls included more than 100,000 non-traditional computing devices, including home-networking routers, multimedia centers and at least one refrigerator, according to California Software-as-a-Service provider Proofpoint, Inc. Most of the botnet identified by Proofpoint as having been used for the attack are traditional IT devices. About a quarter of the total, however, are connected devices often referred to collectively as the Internet of Things, and which Proofpoint nicknamed "Thingbots." The attack is the first documented case of a genuine large-scale criminal act committed using compromised security in semi-intelligent Things, though security experts including Bruce Schneier have warned that the IoT is inherently insecure and that the tendency of consumers to be lax about privacy and security transforms wearable or personal computing devices into ready-made 24-hour surveillance networks, waiting to be taken over by the first hacker able to crack the digital security protecting a well-equipped Maytag. The attacks launched through the Thingbots weren't unsophisticated, however. The 750,000 malicious emails launched around the end-of-year holidays came from 450,000 unique IP addresses, 100,000 of which belonged to IoT devices: mostly home routers and networked-storage devices, but also cable set-top boxes (Dreambox, VU Duo2 Plus, Melita Cable HD), plus a number of gaming consoles, smart TVs, media centers and smart appliances. "This proof of a systematic compromise of IoT devices and it subsequent use of those Thingbots to further attack other networks is something we've never seen before," the Proofpoint report concluded. "[It] suggests an unfortunate future for both home users and enterprises, the latter of which now faces an even larger volume of malicious attack capacity." Though vast increases in the number of potential spambots is disconcerting enough, Thingbots pose the threat of direct attack or infection inside the corporate firewall as well. "All a user has to do is use a remote RDP connection, or conceivably simply take an action like checking their fridge from their work PC," the Proofpoint report found in describing how attackers could use Thingbots as jumping-off points to other attacks. "If a classic drive-by or even a redirect has been installed, the work PC is now compromised (though this is arguably more farfetched). Clearly, as the trend towards smart devices and BYOD increases, the risk of Enterprise exposure increases correspondingly, exponentially." Though "vast numbers" of the compromised devices run versions of embedded Linux (usually busybox), many lacked any password protection at all. Huge numbers used only default username/password combinations installed by manufacturers and which are easily identifiable by Web searches. Worse, Thingbot-based spam networks may be harder to shut down at the source than traditional botnets. Manufacturers have little incentive to add security, and are reluctant to use even low-level default security on many of the devices, the report found. And consumers (unlike, arguably, consumer or business PC users) have little incentive to add their own passwords or other security, and have almost no way to know when a device has been compromised, according to Michael Osterman, analyst at Osterman Research, who was quoted in the Proofpoint materials. "Our conclusion?" the Proofpoint report asks. "Further reiteration that the traditional Enterprise security approach to blocking entry of attacks solely at the email gateway won't work; rather, focus should be on protecting the users at point of click (wherever that may be) and providing insight into user actions and attacker targeting." Image:Shutterstock.com/ rimira
"Smart" tvs are among the 100K non-PCs turned my malware into Thingbots.[/caption] More than a quarter of the 750,000 malicious emails sent by a sophisticated botnet during the last days of 2013 were sent not by malware-addled zombie computers, but by "Thingbots": Malware-addled zombie computers built into consumer electronics and other "smart" gadgets or appliances. A new report found that more than 750,000 phishing and spam messages sent between Dec. 23 and Jan. 6 turned out to originate from a botnet whose thralls included more than 100,000 non-traditional computing devices, including home-networking routers, multimedia centers and at least one refrigerator, according to California Software-as-a-Service provider Proofpoint, Inc. Most of the botnet identified by Proofpoint as having been used for the attack are traditional IT devices. About a quarter of the total, however, are connected devices often referred to collectively as the Internet of Things, and which Proofpoint nicknamed "Thingbots." The attack is the first documented case of a genuine large-scale criminal act committed using compromised security in semi-intelligent Things, though security experts including Bruce Schneier have warned that the IoT is inherently insecure and that the tendency of consumers to be lax about privacy and security transforms wearable or personal computing devices into ready-made 24-hour surveillance networks, waiting to be taken over by the first hacker able to crack the digital security protecting a well-equipped Maytag. The attacks launched through the Thingbots weren't unsophisticated, however. The 750,000 malicious emails launched around the end-of-year holidays came from 450,000 unique IP addresses, 100,000 of which belonged to IoT devices: mostly home routers and networked-storage devices, but also cable set-top boxes (Dreambox, VU Duo2 Plus, Melita Cable HD), plus a number of gaming consoles, smart TVs, media centers and smart appliances. "This proof of a systematic compromise of IoT devices and it subsequent use of those Thingbots to further attack other networks is something we've never seen before," the Proofpoint report concluded. "[It] suggests an unfortunate future for both home users and enterprises, the latter of which now faces an even larger volume of malicious attack capacity." Though vast increases in the number of potential spambots is disconcerting enough, Thingbots pose the threat of direct attack or infection inside the corporate firewall as well. "All a user has to do is use a remote RDP connection, or conceivably simply take an action like checking their fridge from their work PC," the Proofpoint report found in describing how attackers could use Thingbots as jumping-off points to other attacks. "If a classic drive-by or even a redirect has been installed, the work PC is now compromised (though this is arguably more farfetched). Clearly, as the trend towards smart devices and BYOD increases, the risk of Enterprise exposure increases correspondingly, exponentially." Though "vast numbers" of the compromised devices run versions of embedded Linux (usually busybox), many lacked any password protection at all. Huge numbers used only default username/password combinations installed by manufacturers and which are easily identifiable by Web searches. Worse, Thingbot-based spam networks may be harder to shut down at the source than traditional botnets. Manufacturers have little incentive to add security, and are reluctant to use even low-level default security on many of the devices, the report found. And consumers (unlike, arguably, consumer or business PC users) have little incentive to add their own passwords or other security, and have almost no way to know when a device has been compromised, according to Michael Osterman, analyst at Osterman Research, who was quoted in the Proofpoint materials. "Our conclusion?" the Proofpoint report asks. "Further reiteration that the traditional Enterprise security approach to blocking entry of attacks solely at the email gateway won't work; rather, focus should be on protecting the users at point of click (wherever that may be) and providing insight into user actions and attacker targeting." Image:Shutterstock.com/ rimira