[caption id="attachment_14099" align="aligncenter" width="607"]
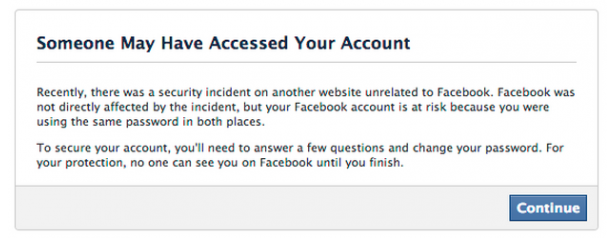
Uh-oh.[/caption] In a bid to protect its own systems from intrusion, Facebook is mining data on Adobe customers. “Facebook users who used the same email and password combinations at both Facebook and Adobe’s site are being asked to change their password and to answer some additional security questions,” KrebsonSecurity
posted Nov. 13. “Facebook spokesman Jay Nancarrow said Facebook is constantly on the lookout for data leaked from other breach incidents that may endanger accounts of its own users.” In October, Adobe reported that it’d
suffered a massive security breach, with cyber-attackers absconding with data on nearly 3 million customers. While that stolen information included customer names, encrypted credit- and debit-card numbers, and data related to customer orders, Adobe insisted that the attackers hadn’t retrieved any decrypted credit- or debit-card numbers. If that wasn’t bad enough, attackers gained illegal access to the source code of various Adobe platforms, including Adobe Acrobat, ColdFusion, and ColdFusion Builder. Adobe claimed it wasn’t aware of any zero-day exploits present in that code. Brian Krebs, who runs KrebsonSecurity, found a 40GB “trove” of Adobe source code parked on a server “used by the same cyber criminals believed to have hacked into major data aggregators earlier this year, including LexisNexis, Dun & Bradstreet and Kroll.” It was assumed (although unconfirmed) that the same attackers targeting the source code also siphoned all that customer information. In the wake of that spectacular hack, Facebook has decided to play defense, using Adobe’s leaked data to determine whether its own systems are at risk from Adobe customers who use the same passwords for Facebook access. In the
comments section of the original Krebs piece, a Facebook engineer explained how company engineers isolated those users who potentially needed to change their password (hat tip to
ZDNet for the head’s up):
“We used the plaintext passwords that had already been worked out by researchers. We took those recovered plaintext passwords and ran them through the same code that we use to check your password at login time. Like Brian’s story indicates, we’re proactive about finding sources of compromised passwords on the Internet. Through practice, we’ve become more efficient and effective at protecting accounts with credentials that have been leaked, and we use an automated process for securing those accounts.”
Users potentially at risk have been seeing the above message. Let this be yet another reminder, kids: keep different passwords for everything.
Image: Facebook  Uh-oh.[/caption] In a bid to protect its own systems from intrusion, Facebook is mining data on Adobe customers. “Facebook users who used the same email and password combinations at both Facebook and Adobe’s site are being asked to change their password and to answer some additional security questions,” KrebsonSecurity posted Nov. 13. “Facebook spokesman Jay Nancarrow said Facebook is constantly on the lookout for data leaked from other breach incidents that may endanger accounts of its own users.” In October, Adobe reported that it’d suffered a massive security breach, with cyber-attackers absconding with data on nearly 3 million customers. While that stolen information included customer names, encrypted credit- and debit-card numbers, and data related to customer orders, Adobe insisted that the attackers hadn’t retrieved any decrypted credit- or debit-card numbers. If that wasn’t bad enough, attackers gained illegal access to the source code of various Adobe platforms, including Adobe Acrobat, ColdFusion, and ColdFusion Builder. Adobe claimed it wasn’t aware of any zero-day exploits present in that code. Brian Krebs, who runs KrebsonSecurity, found a 40GB “trove” of Adobe source code parked on a server “used by the same cyber criminals believed to have hacked into major data aggregators earlier this year, including LexisNexis, Dun & Bradstreet and Kroll.” It was assumed (although unconfirmed) that the same attackers targeting the source code also siphoned all that customer information. In the wake of that spectacular hack, Facebook has decided to play defense, using Adobe’s leaked data to determine whether its own systems are at risk from Adobe customers who use the same passwords for Facebook access. In the comments section of the original Krebs piece, a Facebook engineer explained how company engineers isolated those users who potentially needed to change their password (hat tip to ZDNet for the head’s up):
Uh-oh.[/caption] In a bid to protect its own systems from intrusion, Facebook is mining data on Adobe customers. “Facebook users who used the same email and password combinations at both Facebook and Adobe’s site are being asked to change their password and to answer some additional security questions,” KrebsonSecurity posted Nov. 13. “Facebook spokesman Jay Nancarrow said Facebook is constantly on the lookout for data leaked from other breach incidents that may endanger accounts of its own users.” In October, Adobe reported that it’d suffered a massive security breach, with cyber-attackers absconding with data on nearly 3 million customers. While that stolen information included customer names, encrypted credit- and debit-card numbers, and data related to customer orders, Adobe insisted that the attackers hadn’t retrieved any decrypted credit- or debit-card numbers. If that wasn’t bad enough, attackers gained illegal access to the source code of various Adobe platforms, including Adobe Acrobat, ColdFusion, and ColdFusion Builder. Adobe claimed it wasn’t aware of any zero-day exploits present in that code. Brian Krebs, who runs KrebsonSecurity, found a 40GB “trove” of Adobe source code parked on a server “used by the same cyber criminals believed to have hacked into major data aggregators earlier this year, including LexisNexis, Dun & Bradstreet and Kroll.” It was assumed (although unconfirmed) that the same attackers targeting the source code also siphoned all that customer information. In the wake of that spectacular hack, Facebook has decided to play defense, using Adobe’s leaked data to determine whether its own systems are at risk from Adobe customers who use the same passwords for Facebook access. In the comments section of the original Krebs piece, a Facebook engineer explained how company engineers isolated those users who potentially needed to change their password (hat tip to ZDNet for the head’s up):

