
Which programming language has the most vulnerabilities? WhiteSource, which produces an open-source security and license-compliance platform, recently tried to answer that very question. First, it narrowed down the list of open-source programming languages to seven popular ones: C, Java, JavaScript, Python, Ruby, PHP, and C++. Next, it dug through its own database of open-source vulnerabilities (aggregated in turn from sources such as GitHub and the National Vulnerability Database (NVD)). The organization’s conclusion: C is the most vulnerable open-source language, with 47 percent of all reported vulnerabilities. PHP came in a distant second, with 17 percent, followed by Java with 12 percent, and JavaScript rounding out the top three with 11 percent. 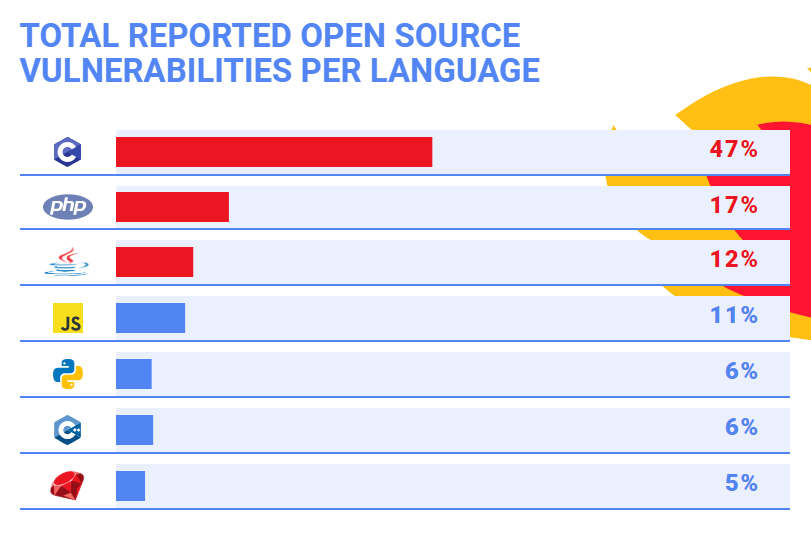 “The high number of open source vulnerabilities in C can be explained by several factors,” the organization added in a blog posting. “For starters, C has been in use for longer than any of the other languages we researched and has the highest volume of written code. It is also one of the languages behind major infrastructure like Open SSL and the Linux kernel. This winning combination of volume and centrality explains the high number of known open source vulnerabilities in C.” In the course of its investigation, WhiteSource also stumbled on something interesting with regard to vulnerability discovery. “There was one trend that stood out across all of the languages, and that’s the substantial rise in the number of known open source security vulnerabilities across all languages over the past two years,” the posting added. “This rise can be explained by the rise in awareness of known security vulnerabilities in open source components, along with the continuously growing popularity of open source.” Bug bounties, in which thousands of tech pros pick through a company’s website to find vulnerabilities, is another potential reason why the number of known security holes has ticked upward in recent years. But that upward trend also raises an unsettling question: how many of these open vulnerabilities are actually being addressed in a timely manner? For tech pros, the rise in vulnerabilities can potentially prove a very good thing—provided they have the skills and experience to squash those bugs whenever (and wherever) they arise. There are lots of un-filled cybersecurity jobs, but many demand certifications such as CEH (Certified Ethical Hacker) or CISA (Certified Information Security Auditor), as well as cutting-edge skills. “Today’s information security teams have to be able to address a wide variety of problems and situations from countering and defending against cyberattacks to participating in the risk management planning efforts of their organization’s business teams,” Nathan Wenzler, the senior director of Cybersecurity at Moss Adams, a Seattle-based accounting, consulting and wealth management firm, recently told Dice. “This means finding well-trained staff across many different disciplines to be part of a complete security program effort. Fortunately, there are just as many varied training and certification programs to help build expertise in whatever area of security you need to address.” For just starting out in security, though, finding and plugging away at bug bounties can be a good way to build experience and learn new skills (and maybe even earn a little cash).
“The high number of open source vulnerabilities in C can be explained by several factors,” the organization added in a blog posting. “For starters, C has been in use for longer than any of the other languages we researched and has the highest volume of written code. It is also one of the languages behind major infrastructure like Open SSL and the Linux kernel. This winning combination of volume and centrality explains the high number of known open source vulnerabilities in C.” In the course of its investigation, WhiteSource also stumbled on something interesting with regard to vulnerability discovery. “There was one trend that stood out across all of the languages, and that’s the substantial rise in the number of known open source security vulnerabilities across all languages over the past two years,” the posting added. “This rise can be explained by the rise in awareness of known security vulnerabilities in open source components, along with the continuously growing popularity of open source.” Bug bounties, in which thousands of tech pros pick through a company’s website to find vulnerabilities, is another potential reason why the number of known security holes has ticked upward in recent years. But that upward trend also raises an unsettling question: how many of these open vulnerabilities are actually being addressed in a timely manner? For tech pros, the rise in vulnerabilities can potentially prove a very good thing—provided they have the skills and experience to squash those bugs whenever (and wherever) they arise. There are lots of un-filled cybersecurity jobs, but many demand certifications such as CEH (Certified Ethical Hacker) or CISA (Certified Information Security Auditor), as well as cutting-edge skills. “Today’s information security teams have to be able to address a wide variety of problems and situations from countering and defending against cyberattacks to participating in the risk management planning efforts of their organization’s business teams,” Nathan Wenzler, the senior director of Cybersecurity at Moss Adams, a Seattle-based accounting, consulting and wealth management firm, recently told Dice. “This means finding well-trained staff across many different disciplines to be part of a complete security program effort. Fortunately, there are just as many varied training and certification programs to help build expertise in whatever area of security you need to address.” For just starting out in security, though, finding and plugging away at bug bounties can be a good way to build experience and learn new skills (and maybe even earn a little cash).
 “The high number of open source vulnerabilities in C can be explained by several factors,” the organization added in a blog posting. “For starters, C has been in use for longer than any of the other languages we researched and has the highest volume of written code. It is also one of the languages behind major infrastructure like Open SSL and the Linux kernel. This winning combination of volume and centrality explains the high number of known open source vulnerabilities in C.” In the course of its investigation, WhiteSource also stumbled on something interesting with regard to vulnerability discovery. “There was one trend that stood out across all of the languages, and that’s the substantial rise in the number of known open source security vulnerabilities across all languages over the past two years,” the posting added. “This rise can be explained by the rise in awareness of known security vulnerabilities in open source components, along with the continuously growing popularity of open source.” Bug bounties, in which thousands of tech pros pick through a company’s website to find vulnerabilities, is another potential reason why the number of known security holes has ticked upward in recent years. But that upward trend also raises an unsettling question: how many of these open vulnerabilities are actually being addressed in a timely manner? For tech pros, the rise in vulnerabilities can potentially prove a very good thing—provided they have the skills and experience to squash those bugs whenever (and wherever) they arise. There are lots of un-filled cybersecurity jobs, but many demand certifications such as CEH (Certified Ethical Hacker) or CISA (Certified Information Security Auditor), as well as cutting-edge skills. “Today’s information security teams have to be able to address a wide variety of problems and situations from countering and defending against cyberattacks to participating in the risk management planning efforts of their organization’s business teams,” Nathan Wenzler, the senior director of Cybersecurity at Moss Adams, a Seattle-based accounting, consulting and wealth management firm, recently told Dice. “This means finding well-trained staff across many different disciplines to be part of a complete security program effort. Fortunately, there are just as many varied training and certification programs to help build expertise in whatever area of security you need to address.” For just starting out in security, though, finding and plugging away at bug bounties can be a good way to build experience and learn new skills (and maybe even earn a little cash).
“The high number of open source vulnerabilities in C can be explained by several factors,” the organization added in a blog posting. “For starters, C has been in use for longer than any of the other languages we researched and has the highest volume of written code. It is also one of the languages behind major infrastructure like Open SSL and the Linux kernel. This winning combination of volume and centrality explains the high number of known open source vulnerabilities in C.” In the course of its investigation, WhiteSource also stumbled on something interesting with regard to vulnerability discovery. “There was one trend that stood out across all of the languages, and that’s the substantial rise in the number of known open source security vulnerabilities across all languages over the past two years,” the posting added. “This rise can be explained by the rise in awareness of known security vulnerabilities in open source components, along with the continuously growing popularity of open source.” Bug bounties, in which thousands of tech pros pick through a company’s website to find vulnerabilities, is another potential reason why the number of known security holes has ticked upward in recent years. But that upward trend also raises an unsettling question: how many of these open vulnerabilities are actually being addressed in a timely manner? For tech pros, the rise in vulnerabilities can potentially prove a very good thing—provided they have the skills and experience to squash those bugs whenever (and wherever) they arise. There are lots of un-filled cybersecurity jobs, but many demand certifications such as CEH (Certified Ethical Hacker) or CISA (Certified Information Security Auditor), as well as cutting-edge skills. “Today’s information security teams have to be able to address a wide variety of problems and situations from countering and defending against cyberattacks to participating in the risk management planning efforts of their organization’s business teams,” Nathan Wenzler, the senior director of Cybersecurity at Moss Adams, a Seattle-based accounting, consulting and wealth management firm, recently told Dice. “This means finding well-trained staff across many different disciplines to be part of a complete security program effort. Fortunately, there are just as many varied training and certification programs to help build expertise in whatever area of security you need to address.” For just starting out in security, though, finding and plugging away at bug bounties can be a good way to build experience and learn new skills (and maybe even earn a little cash). 

